在OpenSUSE 10.3上防止使用Fail2ban进行强力攻击
版本1.0
作者:Falko Timme
在本文中,我将介绍如何在OpenSUSE 10.3系统上安装和配置fail2ban 。 Fail2ban是一种工具,用于观察各种服务(例如SSH,FTP,SMTP,Apache等)的登录尝试,如果从同一个IP地址或主机一次又一次发现登录尝试失败,则fail2ban将停止该IP的进一步登录尝试地址/主机通过使用iptables防火墙规则进行阻止。
本文档不附带任何形式的保证! 我想说,这不是设立这样一个制度的唯一办法。 实现这一目标有很多方法,但这是我所采取的方式。 我不会保证这将为您工作!
1初步说明
Fail2ban类似于本教程中涵盖的DenyHosts : http : //www.youcl.com/preventing_ssh_dictionary_attacks_with_denyhosts ,但与关注SSH的DenyHosts不同,fail2ban可以配置为监视将登录尝试写入日志文件的任何服务,以及而不是使用/etc/hosts.deny来阻止IP地址/主机,fail2ban可以使用iptables和/etc/hosts.deny 。
在此示例中,我将配置fail2ban以监视对SSH服务器,Proftpd服务器,登录尝试.htaccess / .htpasswd保护的网站,到Courier POP3和Courier IMAP以及SASL(用于发送电子邮件)的登录尝试。 我将安装可用于OpenSUSE 10.3的fail2ban软件包。 它配有默认配置,但不幸的是,配置对于大多数上述服务并不适用。 因此,我将创建一个自定义的fail2ban配置,我已经测试,并为我工作。
2安装fail2ban
Fail2ban可从Packman存储库获得,因此我们必须首先启用:
yast2
在YaST,去软件>社区存储库 :
然后激活Packman Repository并点击[Finish] :
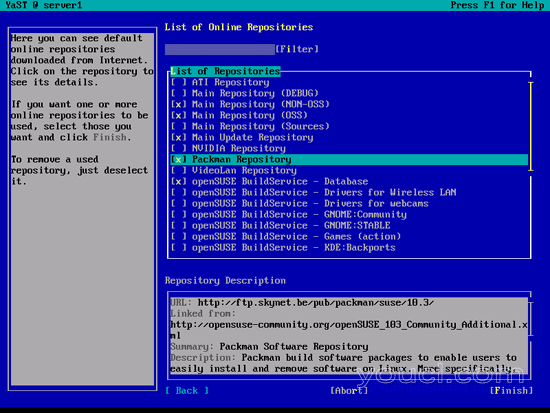
离开YaST之后:
之后fail2ban可以安装如下:
yast2 -i fail2ban
那么我们必须为fail2ban创建系统启动链接并启动它:
chkconfig --add fail2ban
/etc/init.d/fail2ban start
您将在/ etc / fail2ban目录中找到所有fail2ban配置文件。
3配置fail2ban
fail2ban的默认行为在/etc/fail2ban/jail.conf文件中配置 。 看看它,这不难理解。 有一个[DEFAULT]部分适用于所有其他部分,除非默认选项在其他部分中覆盖。
我在这里解释一些配置选项:
-
ignoreip:这是一个空格分隔的IP地址列表,不能被fail2ban阻止。 例如,如果连接到服务器的计算机具有静态IP地址,则可能需要在此处列出。 -
bantime:如果被fail2ban(600秒= 10分钟)捕获,主机被阻止的时间(秒)。 -
maxretry:最大 主机被fail2ban阻止之前失败的登录尝试次数。 -
过滤器:指在/etc/fail2ban/filter.d中的相应过滤器文件。 -
action:指在/etc/fail2ban/action.d中的相应操作文件。 -
logpath:fail2ban检查失败的登录尝试的日志文件。
这是我的/etc/fail2ban/jail.conf文件:
vi /etc/fail2ban/jail.conf
# Fail2Ban configuration file
#
# Author: Cyril Jaquier
#
# $Revision: 611 $
#
# The DEFAULT allows a global definition of the options. They can be override
# in each jail afterwards.
[DEFAULT]
# "ignoreip" can be an IP address, a CIDR mask or a DNS host. Fail2ban will not
# ban a host which matches an address in this list. Several addresses can be
# defined using space separator.
ignoreip = 127.0.0.1 192.168.0.99
# "bantime" is the number of seconds that a host is banned.
bantime = 600
# A host is banned if it has generated "maxretry" during the last "findtime"
# seconds.
findtime = 600
# "maxretry" is the number of failures before a host get banned.
maxretry = 3
# "backend" specifies the backend used to get files modification. Available
# options are "gamin", "polling" and "auto". This option can be overridden in
# each jail too (use "gamin" for a jail and "polling" for another).
#
# gamin: requires Gamin (a file alteration monitor) to be installed. If Gamin
# is not installed, Fail2ban will use polling.
# polling: uses a polling algorithm which does not require external libraries.
# auto: will choose Gamin if available and polling otherwise.
backend = auto
# This jail corresponds to the standard configuration in Fail2ban 0.6.
# The mail-whois action send a notification e-mail with a whois request
# in the body.
[ssh-iptables]
enabled = true
filter = sshd
action = iptables[name=SSH, port=ssh, protocol=tcp]
sendmail-whois[name=SSH, dest=you@mail.com, sender=fail2ban@mail.com]
logpath = /var/log/messages
maxretry = 5
[proftpd-iptables]
enabled = true
filter = proftpd
action = iptables[name=ProFTPD, port=ftp, protocol=tcp]
sendmail-whois[name=ProFTPD, dest=you@mail.com]
logpath = /var/log/messages
maxretry = 6
# This jail forces the backend to "polling".
[sasl-iptables]
enabled = true
filter = sasl
backend = polling
action = iptables[name=sasl, port=smtp, protocol=tcp]
sendmail-whois[name=sasl, dest=you@mail.com]
logpath = /var/log/mail
# Here we use TCP-Wrappers instead of Netfilter/Iptables. "ignoreregex" is
# used to avoid banning the user "myuser".
[ssh-tcpwrapper]
enabled = false
filter = sshd
action = hostsdeny
sendmail-whois[name=SSH, dest=you@mail.com]
ignoreregex = for myuser from
logpath = /var/log/messages
# This jail demonstrates the use of wildcards in "logpath".
# Moreover, it is possible to give other files on a new line.
[apache-tcpwrapper]
enabled = true
filter = apache-auth
action = hostsdeny
logpath = /var/log/apache2/error_log
maxretry = 6
# The hosts.deny path can be defined with the "file" argument if it is
# not in /etc.
[postfix-tcpwrapper]
enabled = true
filter = postfix
action = hostsdeny
sendmail[name=Postfix, dest=you@mail.com]
logpath = /var/log/mail
bantime = 300
# Do not ban anybody. Just report information about the remote host.
# A notification is sent at most every 600 seconds (bantime).
[vsftpd-notification]
enabled = false
filter = vsftpd
action = sendmail-whois[name=VSFTPD, dest=you@mail.com]
logpath = /var/log/messages
maxretry = 5
bantime = 1800
# Same as above but with banning the IP address.
[vsftpd-iptables]
enabled = false
filter = vsftpd
action = iptables[name=VSFTPD, port=ftp, protocol=tcp]
sendmail-whois[name=VSFTPD, dest=you@mail.com]
logpath = /var/log/messages
maxretry = 5
bantime = 1800
# Ban hosts which agent identifies spammer robots crawling the web
# for email addresses. The mail outputs are buffered.
[apache-badbots]
enabled = true
filter = apache-badbots
action = iptables-multiport[name=BadBots, port="http,https"]
sendmail-buffered[name=BadBots, lines=5, dest=you@mail.com]
logpath = /var/log/apache2/access_log
bantime = 172800
maxretry = 1
[courierpop3]
enabled = true
port = pop3
filter = courierlogin
action = iptables[name=%(__name__)s, port=%(port)s]
logpath = /var/log/mail
maxretry = 5
[courierimap]
enabled = true
port = imap2
filter = courierlogin
action = iptables[name=%(__name__)s, port=%(port)s]
logpath = /var/log/mail
maxretry = 5 |
我的客户端计算机具有静态IP地址192.168.0.99 ,并且因为我不想被锁定,我已经将它添加到了ignoreip列表。
我想控制登录尝试SSH,Apache,Proftpd,Courier-POP3,Courier-IMAP和Sasl,所以我设置为这些服务设置为true ,对所有其他服务为false 。 请注意,某些服务(如SSH)可能会被iptables或TCPWrappers( /etc/hosts.deny )阻止。 决定你喜欢哪种方法。
确保使用您自己的电子邮件地址替换电子邮件地址you@mail.com ,以便当有人被fail2ban阻止时收到通知。
如果将文件与默认的/etc/fail2ban/jail.conf进行比较,您还会注意到,由于默认的/etc/fail2ban/jail.conf中的日志文件对于OpenSUSE是不正确的,所以我更改了一些日志文件10.3。
每当我们修改fail2ban配置时,我们必须重新启动fail2ban,所以这是我们现在所做的:
/etc/init.d/fail2ban restart
已经这样了 Fail2ban登录到/var/log/fail2ban.log ,以便您可以检查该文件,以确定/什么主机被阻止。 如果主机被fail2ban阻止,它看起来像这样:
2007-10-07 17:49:09,466 fail2ban.actions: WARNING [apache-tcpwrapper] Ban 1.2.3.4
2007-10-07 18:08:33,213 fail2ban.actions: WARNING [sasl-iptables] Ban 1.2.3.4
2007-10-07 18:26:37,769 fail2ban.actions: WARNING [courierlogin] Ban 1.2.3.4
2007-10-07 18:39:06,765 fail2ban.actions: WARNING [courierimap] Ban 1.2.3.4
您还可以检查防火墙,看看是否有任何主机被阻止。 只需运行
iptables -L
对于使用TCPWrappers阻止主机的服务,请查看/etc/hosts.deny 。
链接
- Fail2ban: http : //www.fail2ban.org
- OpenSUSE: http : //www.opensuse.org








