在本教程中,我们将学习如何使用FreeBSD 11.x中 的加密提供的TLS / SSL证书来保护Apache HTTP服务器。 我们还将介绍如何使Lets加密的证书续展过程自动化。
Apache Web服务器使用TLS / SSL证书来加密端点节点之间的通信,也可以在服务器与客户端之间进行通信,以提供安全性。 让我们加密提供cerboot命令行实用程序,这是一个可以方便您免费获取可信证书的方式的应用程序。
要求:
第1步:在FreeBSD上配置Apache SSL
1.在开始安装certbot实用程序并为Apache创建TSL配置文件之前,首先通过发出以下命令,在Apache根配置目录中创建名为sites-available和sites-enabled的两个不同的目录。
这两个目录的目的是为了方便系统中的虚拟主机配置管理,而不需要在每次添加新的虚拟主机时修改主Apache httpd.conf配置文件。
# mkdir /usr/local/etc/apache24/sites-available # mkdir /usr/local/etc/apache24/sites-enabled
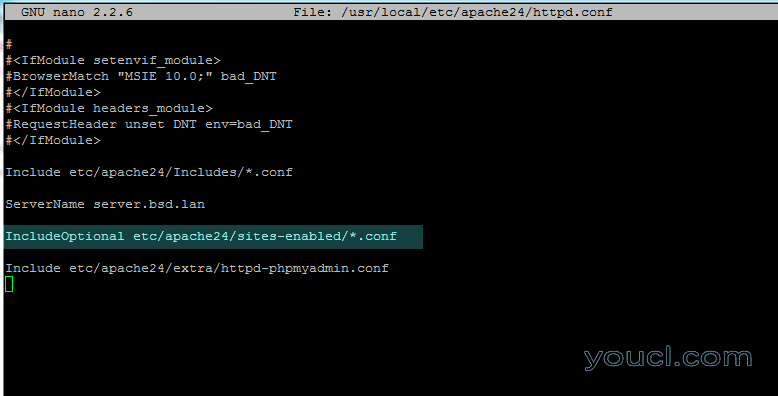
2.创建完两个目录后,使用文本编辑器打开Apache httpd.conf文件,并将以下行添加到文件的末尾,如下所示。
# nano /usr/local/etc/apache24/httpd.conf
添加以下行:
IncludeOptional etc/apache24/sites-enabled/*.conf
在FreeBSD上配置Apache
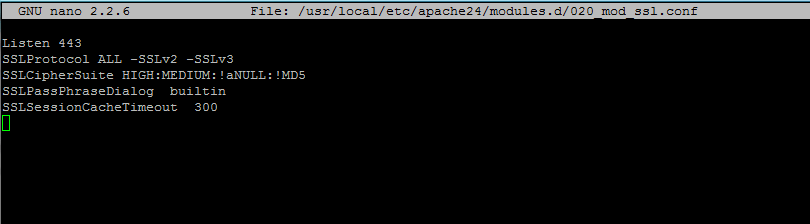
3.接下来,通过在modules.d目录中创建以下内容,创建以下名为020_mod_ssl.conf的新文件,以启用Apache的TLS模块。
# nano /usr/local/etc/apache24/modules.d/020_mod_ssl.conf
将以下行添加到文件020_mod_ssl.conf 。
Listen 443 SSLProtocol ALL -SSLv2 -SSLv3 SSLCipherSuite HIGH:MEDIUM:!aNULL:!MD5 SSLPassPhraseDialog builtin SSLSessionCacheTimeout 300
FreeBSD上的Apache SSL配置
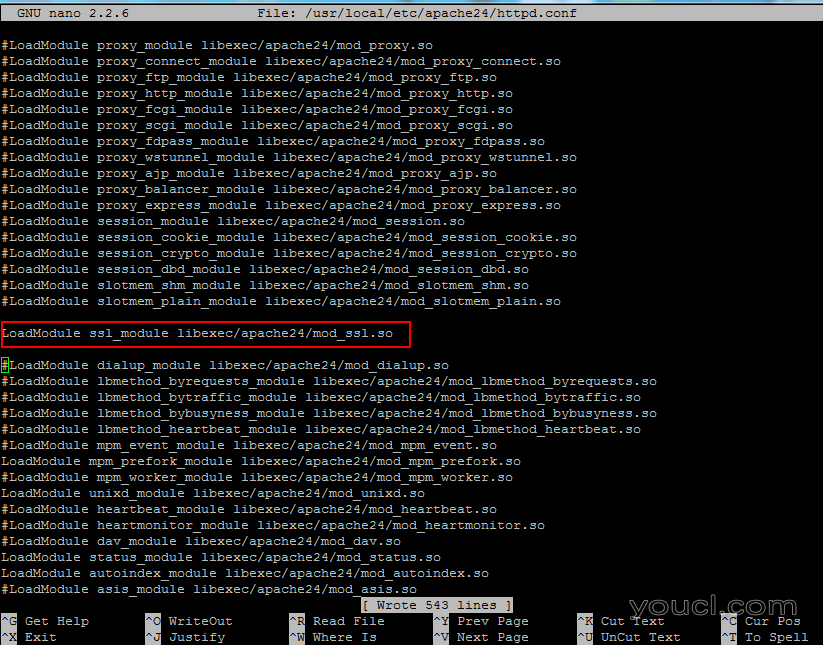
4.现在,从/usr/local/etc/apache24/httpd.conf文件中删除SSL模块的注释,如下所示从以下行的开头移除主题标签:
LoadModule ssl_module libexec/apache24/mod_ssl.so
启用Apache上的SSL模块
5.接下来,在site-available目录中为您的域创建TLS配置文件,最好使用域名,如以下摘录所示:
# nano /usr/local/etc/apache24/sites-available/bsd.lan-ssl.conf
将以下虚拟机配置添加到文件bsd.lan-ssl.conf 。
<VirtualHost *:443>
ServerName www.yourdomain.com
ServerAlias yourdomain.com
DocumentRoot "/usr/local/www/apache24/data/"
SSLEngine on
SSLCertificateFile "/usr/local/etc/letsencrypt/live/www.yourdomain.com/cert.pem"
SSLCertificateKeyFile "/usr/local/etc/letsencrypt/live/www.yourdomain.com/privkey.pem"
SSLCertificateChainFile "/usr/local/etc/letsencrypt/live/www.yourdomain.com/fullchain.pem"
<FilesMatch "\.(cgi|shtml|phtml|php)$">
SSLOptions +StdEnvVars
</FilesMatch>
<Directory "/usr/local/www/apache24/cgi-bin">
SSLOptions +StdEnvVars
</Directory>
BrowserMatch "MSIE [2-5]" \
nokeepalive ssl-unclean-shutdown \
downgrade-1.0 force-response-1.0
CustomLog "/var/log/apache/httpd-ssl_request.log" \
"%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%r\" %b"
<Directory "/usr/local/www/apache24/data/">
Options Indexes FollowSymLinks MultiViews
#AllowOverride controls what directives may be placed in .htaccess files.
AllowOverride All
#Controls who can get stuff from this server file
Require all granted
</Directory>
ErrorLog "/var/log/apache/yourdomain.ssl-error.log"
CustomLog "/var/log/apache/yourdomain.ssl-access_log" combined
</VirtualHost>
Makre确保相应地从ServerName , ServerAlias , ErrorLog , CustomLog语句替换域名变量。
第3步:在FreeBSD上安装Lets'Encrypt
6.在下一步中,发出以下命令,以安装Let's Encrypt提供的certbot实用程序,用于为您的域获取Apache TSL免费证书。
在安装certbot的同时,屏幕上会显示一系列提示。 使用以下屏幕截图配置certbot实用程序。 此外,根据您的机器资源,编译和安装certbot实用程序可能需要一些时间。
# cd /usr/ports/security/py-certbot # make install clean
在FreeBSD上安装Certbot
7.编译过程完成后,发出以下命令,以更新certbot实用程序和certbot所需的依赖关系。
# pkg install py27-certboot # pkg install py27-acme
8.为了生成您的域的证书,请按以下说明发出命令。 确保使用-w标志提供您的网站文件存储在文件系统中的正确的webroot位置(来自您的域配置文件的DocumentRoot指令)。 如果您有多个子域,请将其全部添加到-d标志。
# certbot certonly --webroot -w /usr/local/www/apache24/data/ -d yourdomain.com -d www.yourdomain.com
在获得证书的同时,提供电子邮件地址进行证书更新,按a同意我们加密条款和条件,并且n不共享电子邮件地址让我们加密合作伙伴。
Saving debug log to /var/log/letsencrypt/letsencrypt.log Enter email address (used for urgent renewal and security notices) (Enter 'c' to cancel):[email protected] There seem to be problems with that address. Enter email address (used for urgent renewal and security notices) If you really want to skip this, you can run the client with --register-unsafely-without-email but make sure you then backup your account key from /etc/letsencrypt/accounts (Enter 'c' to cancel):[email protected] ------------------------------------------------------------------------------- Please read the Terms of Service at https://letsencrypt.org/documents/LE-SA-v1.1.1-August-1-2016.pdf. You must agree in order to register with the ACME server at https://acme-v01.api.letsencrypt.org/directory ------------------------------------------------------------------------------- (A)gree/(C)ancel:a------------------------------------------------------------------------------- Would you be willing to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We'd like to send you email about EFF and our work to encrypt the web, protect its users and defend digital rights. ------------------------------------------------------------------------------- (Y)es/(N)o:nObtaining a new certificate Performing the following challenges: http-01 challenge for www.domain.com Using the webroot path /usr/local/www/apache24/data for all unmatched domains. Waiting for verification... Cleaning up challenges IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at /usr/local/etc/letsencrypt/live/www.yourdomain.com/fullchain.pem. Your cert will expire on 2017-11-15. To obtain a new or tweaked version of this certificate in the future, simply run certbot again. To non-interactively renew *all* of your certificates, run "certbot renew" - Your account credentials have been saved in your Certbot configuration directory at /usr/local/etc/letsencrypt. You should make a secure backup of this folder now. This configuration directory will also contain certificates and private keys obtained by Certbot so making regular backups of this folder is ideal. - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF: https://eff.org/donate-le
9.获取域的证书后,您可以运行 ,以列出以下示例中所示的所有证书组件(链,私钥,证书)。
# ls -al /usr/local/etc/letsencrypt/live/www.yourdomain.com/
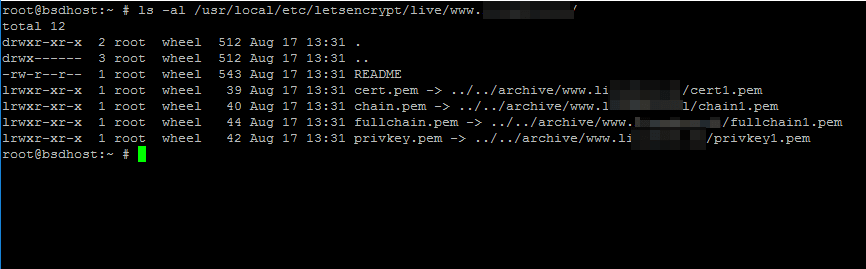
列出域证书和密钥
第3步:在FreeBSD上更新Apache TLS证书
10.为了添加让我们将证书加密到您的网站,打开您的域的apache配置文件,并更新以下行以反映颁发证书的路径。
# nano /usr/local/etc/apache24/sites-available/bsd.lan-ssl.conf
添加这些TLS证书行:
SSLCertificateFile "/usr/local/etc/letsencrypt/live/www.yourdomain.com/cert.pem" SSLCertificateKeyFile "/usr/local/etc/letsencrypt/live/www.yourdomain.com/privkey.pem" SSLCertificateChainFile "/usr/local/etc/letsencrypt/live/www.yourdomain.com/fullchain.pem"
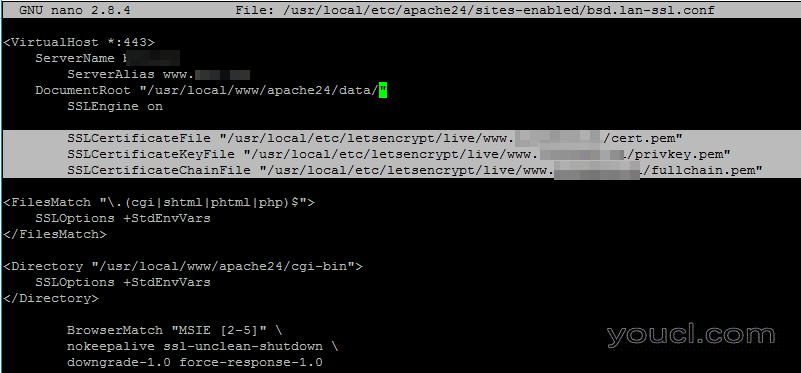
配置域的SSL证书
11.最后,启用TLS配置文件,通过为您的域TLS配置文件创建一个符号链接到启用了站点的目录,检查Apache配置是否有可能的语法错误,如果语法正常,则通过发出以下命令重新启动Apache守护程序。
# ln -sf /usr/local/etc/apache24/sites-available/bsd.lan-ssl.conf /usr/local/etc/apache24/sites-enabled/ # apachectl -t # service apache24 restart
12.为了检查Apache服务是否正在监听HTTPS端口443 ,请执行以下命令列出httpd网络套接字。
# sockstat -4 | grep httpd
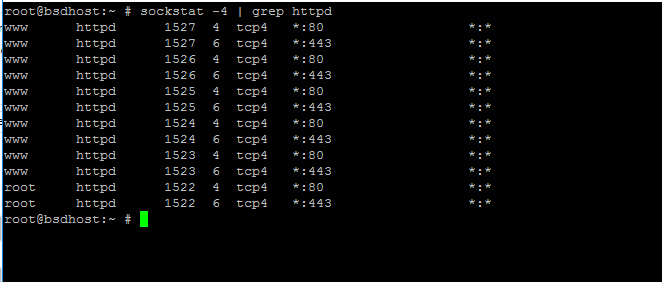
检查Apache端口
13.您可以通过HTTPS协议从浏览器导航到您的域名,以确认我们的加密证书是否成功应用。
https://www.yourdomain.com
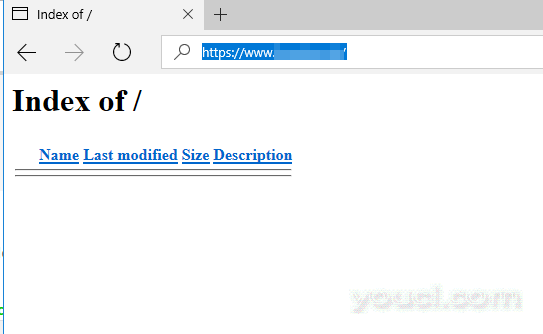
验证HTTPS我们加密证书
14.为了从命令行获取有关发出的Let's Encrypt证书的额外信息,请使用openssl命令,如下所示。
# openssl s_client -connect www.yourdomain.com:443
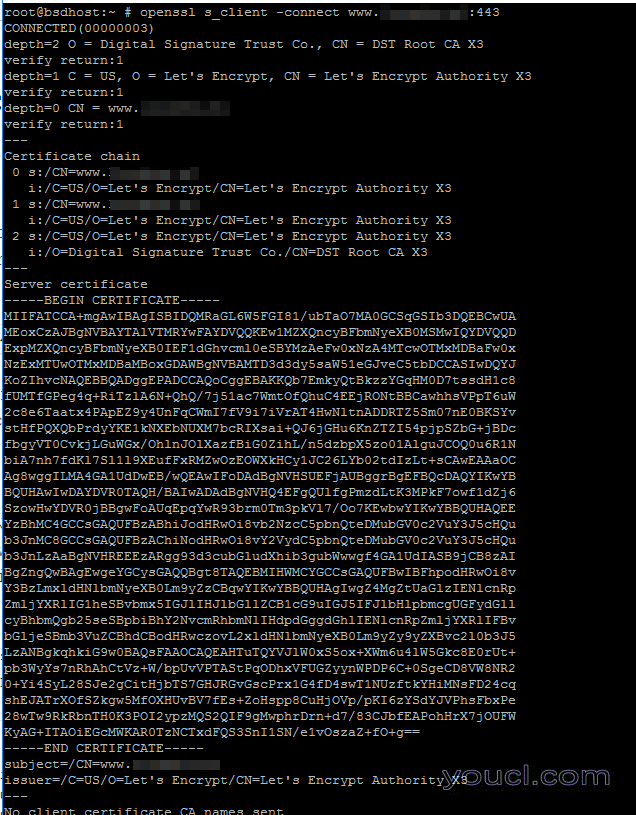
检查我们加密证书信息
您还可以验证流量是否使用Let's Encrypt CA从移动设备提供的有效证书进行加密 ,如下面的移动屏幕截图所示。
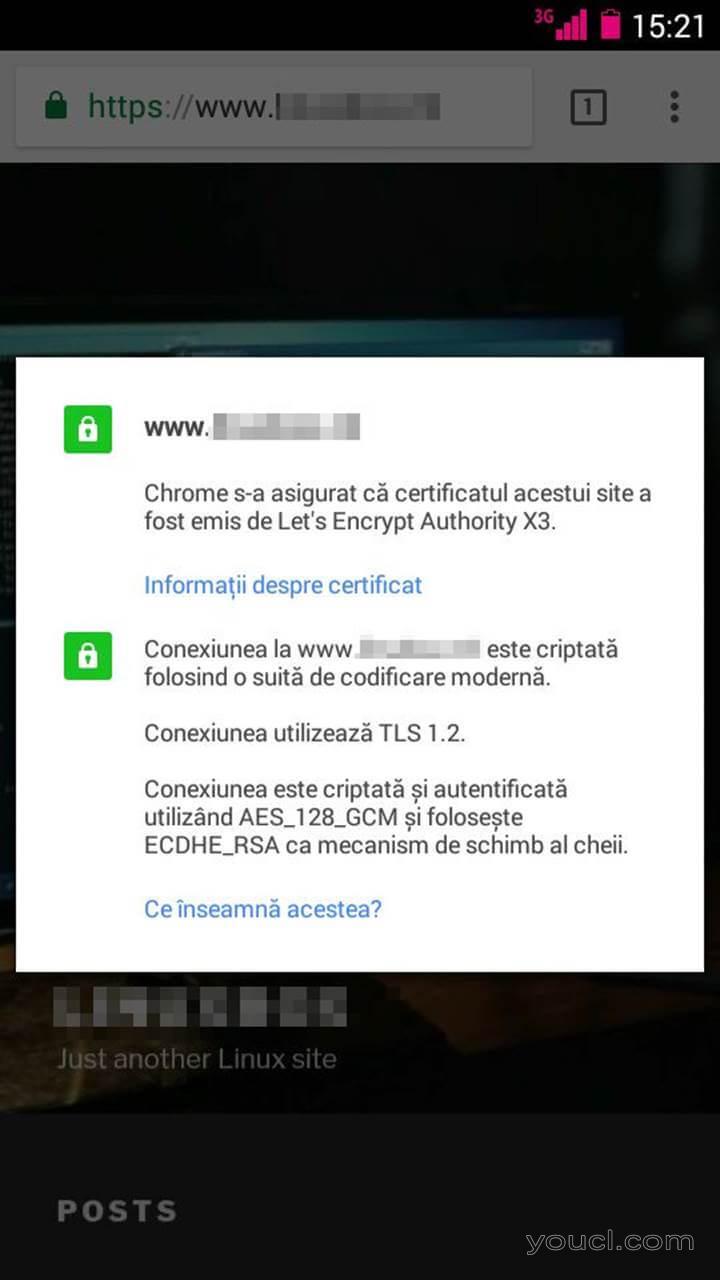
验证允许加密HTTPS流量
就这样! 客户端现在可以安全地访问您的网站,因为在服务器和客户端的浏览器之间流动的流量被加密。 有关certbot实用程序的更复杂的任务,请访问以下链接: https ://certbot.eff.org/








