本文是关于第2层隧道协议(L2TP)与IPSec提供端到端加密在第2层VPN,因为安全功能在L2TP不可用。 IPsec的开源实现是StrongSwan和OpenSwan,都在所有Linux发行版上都支持。 在本教程中,OpenSwan用于为L2TP VPN提供安全通道。 Freeradius是一个着名的开源工具,为用户提供不同类型的身份验证。 Freeradius用于在建立安全通道之前验证L2TP VPN用户。 一个基于Android的客户端将被用于基于L2TP的安全隧道。
安装所需的软件包
以下重要软件包将安装在Ubuntu 16.04 LTS上。
- Freeradius服务器/客户端
- Poptop服务器
- xl2tpd
- Openswan为IPsec
- MySQL服务器/客户端
- 野牛和Flex
- GMP开发库
如下所示,大部分所需的软件包都可以在Ubuntu 16.04 LTS存储库中使用。
apt-get update
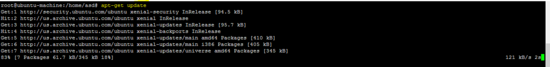
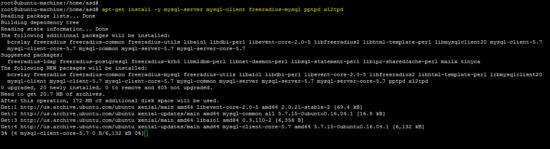
apt-get install -y mysql-server mysql-client freeradius-mysql pptpd xl2tpd
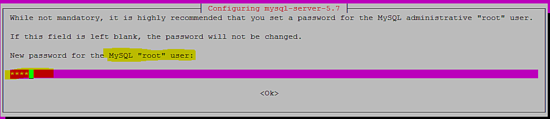
以下屏幕截图显示了在安装过程中如何设置MySQL数据库服务器用户“root”的密码。
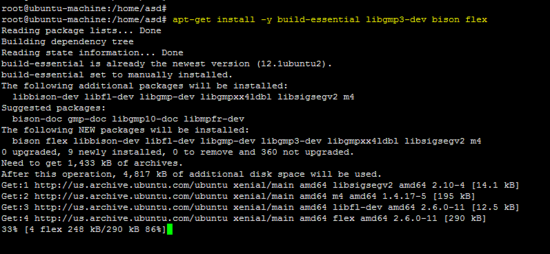
从Ubuntu 16.04平台的源代码开始,OpenSwan安装需要以下软件包。
apt-get install -y build-essential libgmp3-dev bison flex
Freeradius客户端和OpenSwan软件包在存储库中不可用,因此这两种工具都已经从源安装。
安装Freeradius客户端
从以下链接下载最新的Freeradius客户端:
wget https://github.com/FreeRADIUS/freeradius-client/archive/master.zip
unzip master.zip
mv freeradius-client-master freeradius-client
cd freeradius-client
首先,使用前缀交换机运行configure脚本,并使用make命令安装软件。
./configure --prefix=/
make && make install
安装OpenSwan
OpenSwan IPsec工具的源代码可在以下链接中找到。 下载档案并解压缩。
wget https://download.openswan.org/openswan/openswan-latest.tar.gz
tar -xzf openswan-latest.tar.gz
cd openswan-*
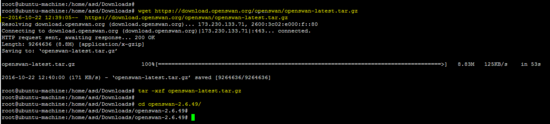
运行以下命令来编译和安装OpenSwan。
make programs
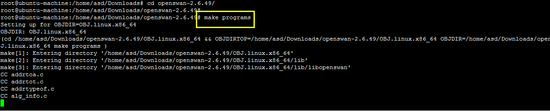
make install
组态
在我们开始配置安装的软件包之前,Ubuntu平台上需要以下基本配置(iptables和sysctl)。
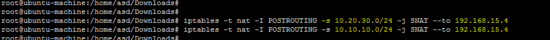
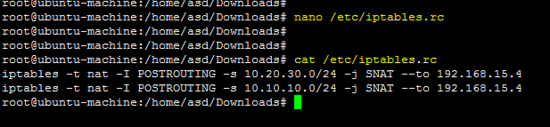
为终端上的两个网络(10.20.30.0/24和10.10.10.0/24)输入以下iptables规则。
iptables -t nat -I POSTROUTING -s 10.20.30.0/24 -j SNAT --to 192.168.15.4
iptables -t nat -I POSTROUTING -s 10.10.10.0/24 -j SNAT --to 192.168.15.4
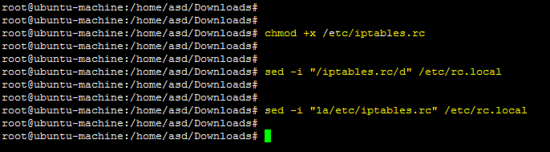
上述规则应保存在/etc/iptables.rc文件中,以便在引导时应用它们。
chmod +x /etc/iptables.rc
sed -i "/iptables.rc/d" /etc/rc.local
sed -i "1a/etc/iptables.rc" /etc/rc.local
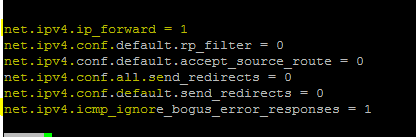
在/etc/sysctl.conf文件中添加以下行以在Linux机器上启用转发。
net.ipv4.ip_forward = 1
net.ipv4.conf.default.rp_filter = 0
net.ipv4.conf.default.accept_source_route = 0
net.ipv4.conf.all.send_redirects = 0
net.ipv4.conf.default.send_redirects = 0
net.ipv4.icmp_ignore_bogus_error_responses = 1
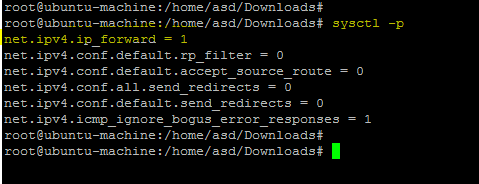
运行以下命令应用更改。
sysctl -p
Freeradius服务器的配置
运行以下命令更改freeradius的密码。
sed -i "s/PASSWORD('radpass')/PASSWORD('test')/g" /etc/freeradius/sql/mysql/admin.sql
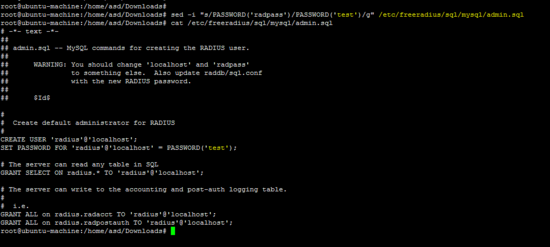
以下MySQL命令将在Ubuntu上配置Freeradius服务器。
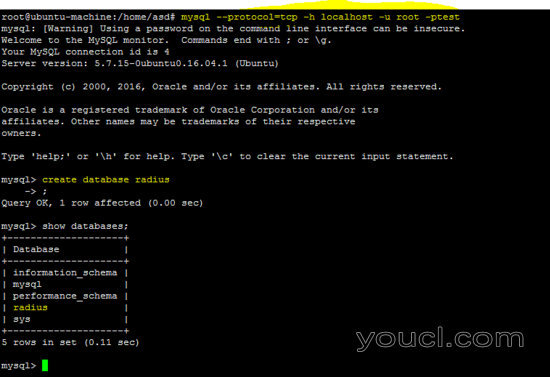
mysql --protocol=tcp -h localhost -u root -ptest
create database radius # create DB radius
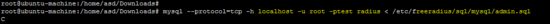
mysql --protocol = tcp -h localhost -u root -ptest radius </etc/freeradius/sql/mysql/admin.sql
mysql --protocol=tcp -h localhost -u root -ptest radius < /etc/freeradius/sql/mysql/cui.sql
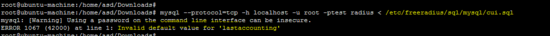
添加适当的日期来修复/etc/freeradius/sql/mysql/cui.sql中的无效默认值问题。
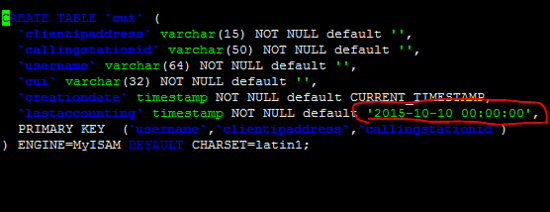
在/etc/freeradius/sql/mysql/cui.sql文件中进行更正后,重新运行以上命令以修复上述错误。
mysql --protocol=tcp -h localhost -u root -ptest radius < /etc/freeradius/sql/mysql/ippool.sql
mysql --protocol=tcp -h localhost -u root -ptest radius < /etc/freeradius/sql/mysql/nas.sql
mysql --protocol=tcp -h localhost -u root -ptest radius < /etc/freeradius/sql/mysql/schema.sql
mysql --protocol=tcp -h localhost -u root -ptest radius < /etc/freeradius/sql/mysql/wimax.sql
运行以下sed命令更改用户“radius”的默认密码。 在本教程中,用户“radius”的密码为“test”。 选择服务器上的安全密码。
sed -i "s/password = \"radpass\"/password = \"test\"/g" /etc/freeradius/sql.conf
在Freeradius服务器的modules目录中为sql配置创建一个软链接。
ln -sf /etc/freeradius/sql.conf /etc/freeradius/modules/sql
Ubuntu 16.04中不存在以下文件,因此,请使用描述的内容创建所有必需的文件。
- / etc / freeradius / modules / hourlylytraffic
- / etc / freeradius / modules / dailytraffic
- / etc / freeradius / modules / monthlytraffic
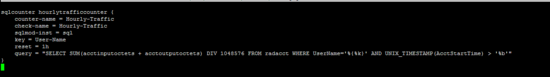
/ etc / freeradius / modules / hourlytraffic
sqlcounter hourlytrafficcounter {
counter-name = Hourly-Traffic
check-name = Hourly-Traffic
sqlmod-inst = sql
key = User-Name
reset = 1h
query = "SELECT SUM(acctinputoctets + acctoutputoctets) DIV 1048576 FROM radacct WHERE UserName='%{%k}' AND UNIX_TIMESTAMP(AcctStartTime) > '%b'"
}
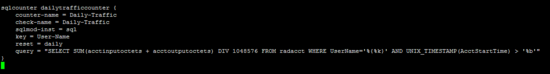
/ etc / freeradius / modules / dailytraffic
sqlcounter dailytrafficcounter {
counter-name = Daily-Traffic
check-name = Daily-Traffic
sqlmod-inst = sql
key = User-Name
reset = daily
query = "SELECT SUM(acctinputoctets + acctoutputoctets) DIV 1048576 FROM radacct WHERE UserName='%{%k}' AND UNIX_TIMESTAMP(AcctStartTime) > '%b'"
}
/ etc / freeradius / modules / monthlytraffic
sqlcounter monthlytrafficcounter {
counter-name = Monthly-Traffic
check-name = Monthly-Traffic
sqlmod-inst = sql
key = User-Name
reset = monthly
query = "SELECT SUM(acctinputoctets + acctoutputoctets) DIV 1048576 FROM radacct WHERE UserName='%{%k}' AND UNIX_TIMESTAMP(AcctStartTime) > '%b'"
}

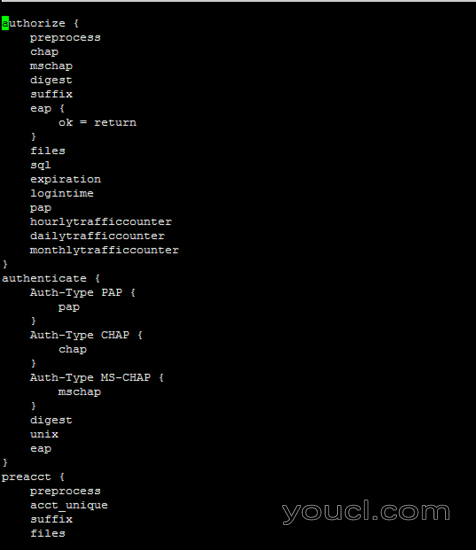
以下文件对于freeradius服务器配置很重要。 我们的运行配置如下。
/ etc / freeradius / sites启用/默认
authorize {
preprocess
chap
mschap
digest
suffix
eap {
ok = return
}
files
sql
expiration
logintime
pap
hourlytrafficcounter
dailytrafficcounter
monthlytrafficcounter
}
authenticate {
Auth-Type PAP {
pap
}
Auth-Type CHAP {
chap
}
Auth-Type MS-CHAP {
mschap
}
digest
unix
eap
}
preacct {
preprocess
acct_unique
suffix
files
}
accounting {
detail
unix
radutmp
sql
exec
attr_filter.accounting_response
}
session {
radutmp
sql
}
post-auth {
sql
exec
Post-Auth-Type REJECT {
attr_filter.access_reject
}
}
pre-proxy {
}
post-proxy {
eap
}
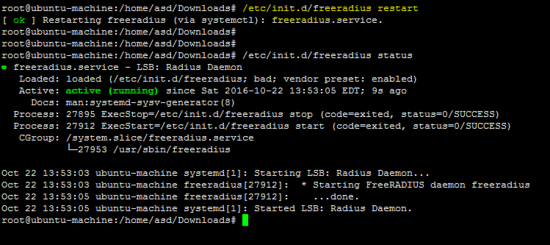
使用以下命令重新启动freeradius服务器并验证配置。
/etc/init.d/freeradius restart
Freeradius客户端的配置
以下命令在freeradius客户端的“servers”文件中设置主机名和密码。
echo -e "localhost\ttesting123" >> /etc/radiusclient/servers
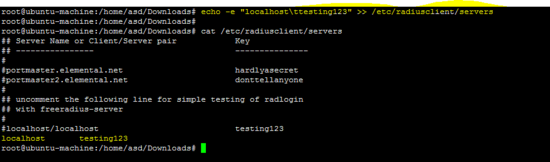
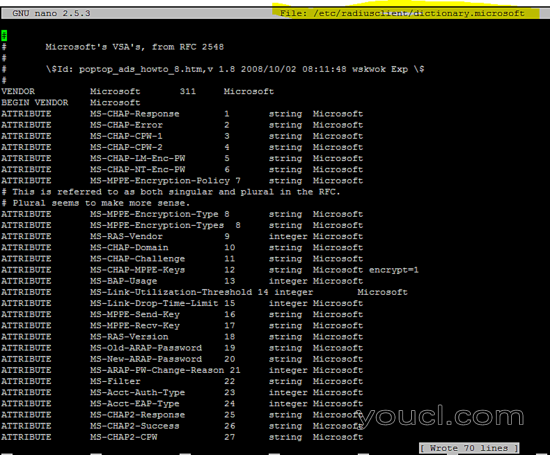
为基于Windows的客户端创建dictionary.microsoft配置文件。
vi /etc/radiusclient/dictionary.microsoft
#
# Microsoft's VSA's, from RFC 2548
#
# \$Id: poptop_ads_howto_8.htm,v 1.8 2008/10/02 08:11:48 wskwok Exp \$
#
VENDOR Microsoft 311 Microsoft
BEGIN VENDOR Microsoft
ATTRIBUTE MS-CHAP-Response 1 string Microsoft
ATTRIBUTE MS-CHAP-Error 2 string Microsoft
ATTRIBUTE MS-CHAP-CPW-1 3 string Microsoft
ATTRIBUTE MS-CHAP-CPW-2 4 string Microsoft
ATTRIBUTE MS-CHAP-LM-Enc-PW 5 string Microsoft
ATTRIBUTE MS-CHAP-NT-Enc-PW 6 string Microsoft
ATTRIBUTE MS-MPPE-Encryption-Policy 7 string Microsoft
# This is referred to as both singular and plural in the RFC.
# Plural seems to make more sense.
ATTRIBUTE MS-MPPE-Encryption-Type 8 string Microsoft
ATTRIBUTE MS-MPPE-Encryption-Types 8 string Microsoft
ATTRIBUTE MS-RAS-Vendor 9 integer Microsoft
ATTRIBUTE MS-CHAP-Domain 10 string Microsoft
ATTRIBUTE MS-CHAP-Challenge 11 string Microsoft
ATTRIBUTE MS-CHAP-MPPE-Keys 12 string Microsoft encrypt=1
ATTRIBUTE MS-BAP-Usage 13 integer Microsoft
ATTRIBUTE MS-Link-Utilization-Threshold 14 integer Microsoft
ATTRIBUTE MS-Link-Drop-Time-Limit 15 integer Microsoft
ATTRIBUTE MS-MPPE-Send-Key 16 string Microsoft
ATTRIBUTE MS-MPPE-Recv-Key 17 string Microsoft
ATTRIBUTE MS-RAS-Version 18 string Microsoft
ATTRIBUTE MS-Old-ARAP-Password 19 string Microsoft
ATTRIBUTE MS-New-ARAP-Password 20 string Microsoft
ATTRIBUTE MS-ARAP-PW-Change-Reason 21 integer Microsoft
ATTRIBUTE MS-Filter 22 string Microsoft
ATTRIBUTE MS-Acct-Auth-Type 23 integer Microsoft
ATTRIBUTE MS-Acct-EAP-Type 24 integer Microsoft
ATTRIBUTE MS-CHAP2-Response 25 string Microsoft
ATTRIBUTE MS-CHAP2-Success 26 string Microsoft
ATTRIBUTE MS-CHAP2-CPW 27 string Microsoft
ATTRIBUTE MS-Primary-DNS-Server 28 ipaddr
ATTRIBUTE MS-Secondary-DNS-Server 29 ipaddr
ATTRIBUTE MS-Primary-NBNS-Server 30 ipaddr Microsoft
ATTRIBUTE MS-Secondary-NBNS-Server 31 ipaddr Microsoft
#ATTRIBUTE MS-ARAP-Challenge 33 string Microsoft
#
# Integer Translations
#
# MS-BAP-Usage Values
VALUE MS-BAP-Usage Not-Allowed 0
VALUE MS-BAP-Usage Allowed 1
VALUE MS-BAP-Usage Required 2
# MS-ARAP-Password-Change-Reason Values
VALUE MS-ARAP-PW-Change-Reason Just-Change-Password 1
VALUE MS-ARAP-PW-Change-Reason Expired-Password 2
VALUE MS-ARAP-PW-Change-Reason Admin-Requires-Password-Change 3
VALUE MS-ARAP-PW-Change-Reason Password-Too-Short 4
# MS-Acct-Auth-Type Values
VALUE MS-Acct-Auth-Type PAP 1
VALUE MS-Acct-Auth-Type CHAP 2
VALUE MS-Acct-Auth-Type MS-CHAP-1 3
VALUE MS-Acct-Auth-Type MS-CHAP-2 4
VALUE MS-Acct-Auth-Type EAP 5
# MS-Acct-EAP-Type Values
VALUE MS-Acct-EAP-Type MD5 4
VALUE MS-Acct-EAP-Type OTP 5
VALUE MS-Acct-EAP-Type Generic-Token-Card 6
VALUE MS-Acct-EAP-Type TLS 13
END-VENDOR Microsoft
vi /etc/radiusclient/dictionary.merit
#
# Experimental extensions, configuration only (for check-items)
# Names/numbers as per the MERIT extensions (if possible).
#
ATTRIBUTE NAS-Identifier 32 string
ATTRIBUTE Proxy-State 33 string
ATTRIBUTE Login-LAT-Service 34 string
ATTRIBUTE Login-LAT-Node 35 string
ATTRIBUTE Login-LAT-Group 36 string
ATTRIBUTE Framed-AppleTalk-Link 37 integer
ATTRIBUTE Framed-AppleTalk-Network 38 integer
ATTRIBUTE Framed-AppleTalk-Zone 39 string
ATTRIBUTE Acct-Input-Packets 47 integer
ATTRIBUTE Acct-Output-Packets 48 integer
# 8 is a MERIT extension.
VALUE Service-Type Authenticate-Only 8
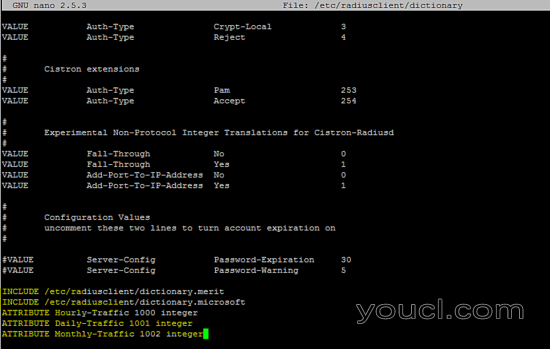
将以下行添加到/ etc / radiusclient / dictionary文件中。
INCLUDE /etc/radiusclient/dictionary.merit
INCLUDE /etc/radiusclient/dictionary.microsoft
ATTRIBUTE Hourly-Traffic 1000 integer
ATTRIBUTE Daily-Traffic 1001 integer
ATTRIBUTE Monthly-Traffic 1002 integer
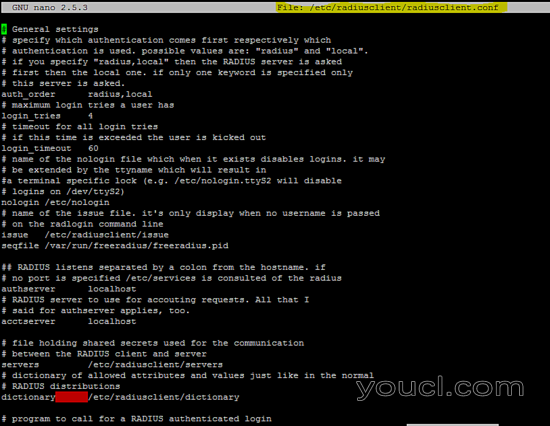
以下是radius客户端的运行配置。
/etc/radiusclient/radiusclient.conf
# General settings
# specify which authentication comes first respectively which
# authentication is used. possible values are: "radius" and "local".
# if you specify "radius,local" then the RADIUS server is asked
# first then the local one. if only one keyword is specified only
# this server is asked.
auth_order radius,local
# maximum login tries a user has
login_tries 4
# timeout for all login tries
# if this time is exceeded the user is kicked out
login_timeout 60
# name of the nologin file which when it exists disables logins. it may
# be extended by the ttyname which will result in
#a terminal specific lock (e.g. /etc/nologin.ttyS2 will disable
# logins on /dev/ttyS2)
nologin /etc/nologin
# name of the issue file. it's only display when no username is passed
# on the radlogin command line
issue /etc/radiusclient/issue
seqfile /var/run/freeradius/freeradius.pid
## RADIUS listens separated by a colon from the hostname. if
# no port is specified /etc/services is consulted of the radius
authserver localhost
# RADIUS server to use for accouting requests. All that I
# said for authserver applies, too.
acctserver localhost
# file holding shared secrets used for the communication
# between the RADIUS client and server
servers /etc/radiusclient/servers
# dictionary of allowed attributes and values just like in the normal
# RADIUS distributions
dictionary /etc/radiusclient/dictionary
# program to call for a RADIUS authenticated login
login_radius /sbin/login.radius
# file which specifies mapping between ttyname and NAS-Port attribute
mapfile /etc/radiusclient/port-id-map
# default authentication realm to append to all usernames if no
# realm was explicitly specified by the user
default_realm
# time to wait for a reply from the RADIUS server
radius_timeout 10
# resend request this many times before trying the next server
radius_retries 3
# local address from which radius packets have to be sent
bindaddr *
# program to execute for local login
# it must support the -f flag for preauthenticated login
login_local /bin/login
/ etc / radiusclient / dictionary文件中的以下配置(与IPv6相关)应该被注释掉以运行radius客户端。
ATTRIBUTE NAS-Filter-Rule 92 string
ATTRIBUTE Originating-Line-Info 94 string
ATTRIBUTE NAS-IPv6-Address 95 string
ATTRIBUTE Framed-Interface-Id 96 string
ATTRIBUTE Framed-IPv6-Prefix 97 ipv6prefix
ATTRIBUTE Login-IPv6-Host 98 string
ATTRIBUTE Framed-IPv6-Route 99 string
ATTRIBUTE Framed-IPv6-Pool 100 string
ATTRIBUTE Error-Cause 101 integer
ATTRIBUTE EAP-Key-Name 102 string
#
# RFC6911 IPv6 attributes
#
ATTRIBUTE Framed-IPv6-Address 168 ipv6addr
ATTRIBUTE DNS-Server-IPv6-Address 169 ipv6addr
ATTRIBUTE Route-IPv6-Information 170 ipv6prefix
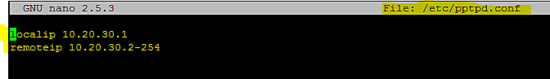
Poptop服务器的配置
在/etc/pptpd.conf文件中添加以下配置。
localip 10.20.30.1
remoteip 10.20.30.2-254
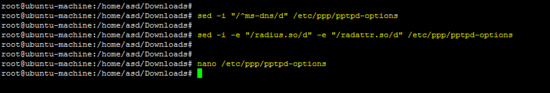
在/ etc / ppp / pptpd-options文件上运行以下sed命令。
sed -i "/^ms-dns/d" /etc/ppp/pptpd-options
sed -i -e "/radius.so/d" -e "/radattr.so/d" /etc/ppp/pptpd-options
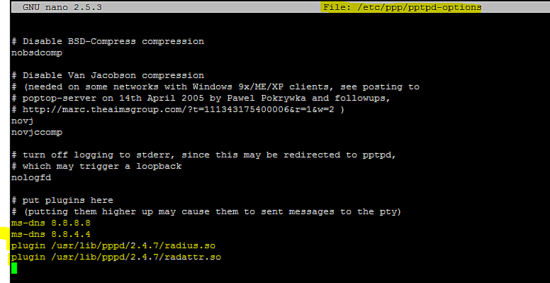
在/ etc / ppp / pptpd-options文件中添加以下行。
ms-dns 8.8.8.8
ms-dns 8.8.4.4
plugin /usr/lib/pppd/2.4.7/radius.so
plugin /usr/lib/pppd/2.4.7/radattr.so
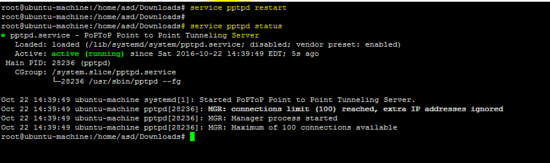
重新启动pptpd服务以应用上述更改。
service pptpd restart
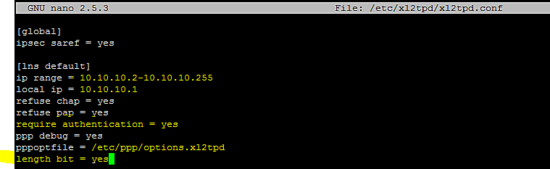
配置xl2tp
在/etc/xl2tpd/xl2tpd.conf文件中包含以下配置行,如下图所示。
[global]
ipsec saref = yes
[lns default]
ip range = 10.10.10.2-10.10.10.255
local ip = 10.10.10.1
refuse chap = yes
refuse pap = yes
require authentication = yes
ppp debug = yes
pppoptfile = /etc/ppp/options.xl2tpd
length bit = yes
OpenSwan的配置
在/etc/ipsec.secrets中添加ipsec秘密文件的以下设置。
192.168.15.4 %any 0.0.0.0: PSK "test"

L2TP隧道的IPsec配置包含在/etc/ipsec.conf文件中。
version 2.0
config setup
nat_traversal=yes
virtual_private=%v4:192.168.0.0/16,%v4:10.0.0.0/8,%v4:172.16.0.0/12,%v4:25.0.0.0/8,%v4:!10.254.253.0/24
protostack=netkey
#protostack=mast # used for SAref + MAST only
interfaces="%defaultroute"
oe=off
conn psk-l2tp
pfs=no
auto=add
rekey=no
# overlapip=yes # for SAref + MAST
# sareftrack=yes # for SAref + MAST
type=transport
left=192.168.15.4
leftprotoport=17/1701
right=%any
rightprotoport=17/%any
rightsubnet=vhost:%priv,%no
authby=secret
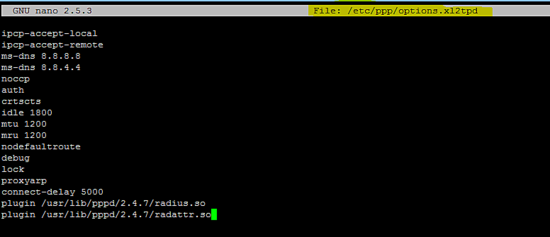
配置PPP服务器
在/etc/ppp/options.xl2tpd文件中添加以下配置。
ipcp-accept-local
ipcp-accept-remote
ms-dns 8.8.8.8
ms-dns 8.8.4.4
noccp
auth
crtscts
idle 1800
mtu 1200
mru 1200
nodefaultroute
debug
lock
proxyarp
connect-delay 5000
plugin /usr/lib/pppd/2.4.7/radius.so
plugin /usr/lib/pppd/2.4.7/radattr.so
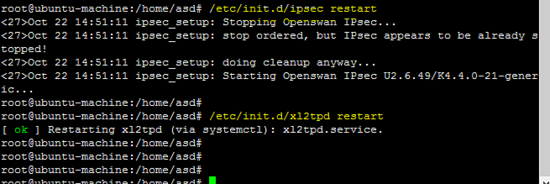
成功配置所有需要的软件包后,现在重新启动所有服务以测试L2TP VPN。
重新启动IPsec&xl2tp服务。
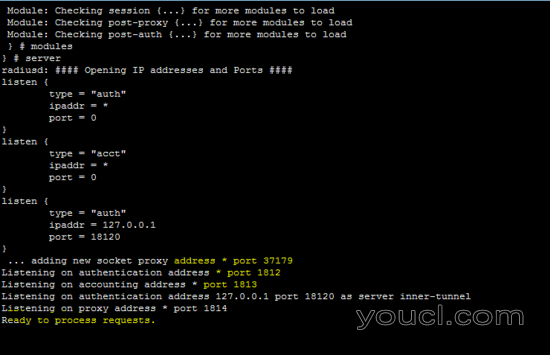
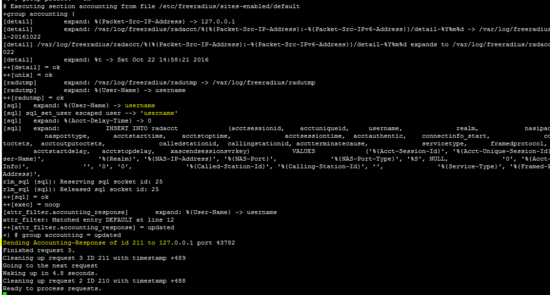
下图显示了freeradius服务器以守护进程模式运行,这有助于确定服务器正在运行。
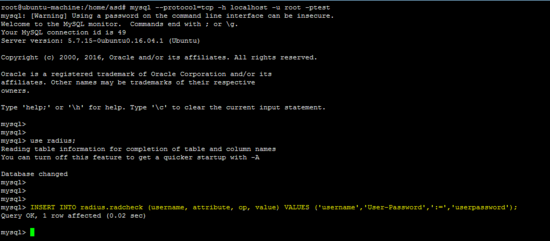
在MySQL数据库中插入用户帐户以测试配置。
INSERT INTO radius.radcheck (username, attribute, op, value) VALUES ('username','User-Password',':=','userpassword');
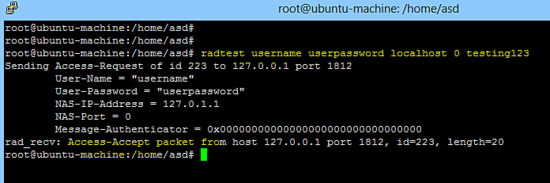
以下命令检查Freeradius服务器是否正在使用本地主机。
radtest username userpassword localhost 0 testing123
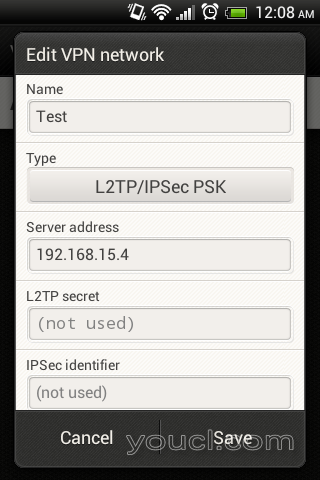
配置L2TP Android客户端
去设置==>更多==> VPN ==>在Android手机上添加VPN网络 ,并创建新的L2TP PSK VPN,如下所示。
创建新的L2TP VPN后,单击它并输入用户名/密码(在freeradius服务器上配置)。
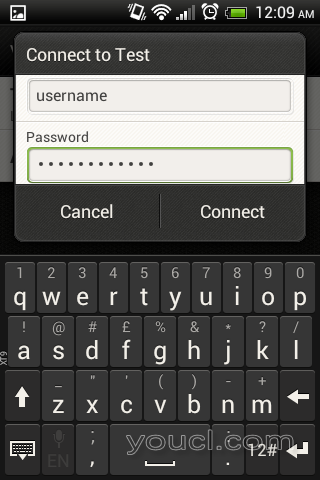
L2TP VPN连接如下图所示。
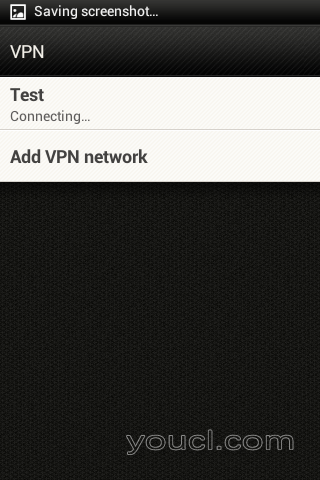
以下屏幕显示L2TP VPN使用Android客户端成功连接。
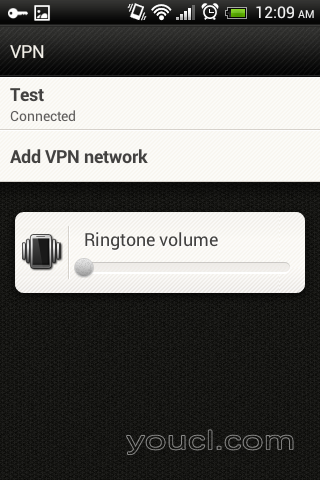
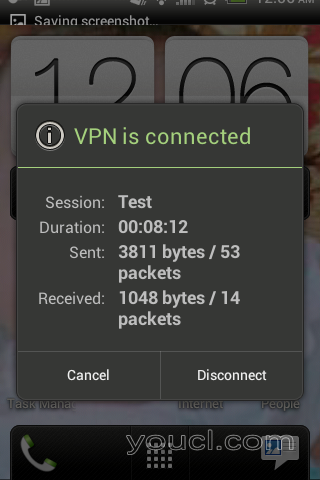
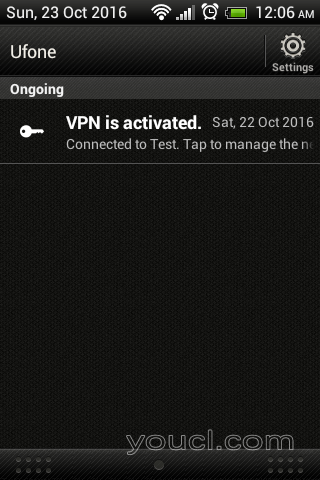
L2TP VPN状态
Freeradius显示L2TP android客户端的成功认证。
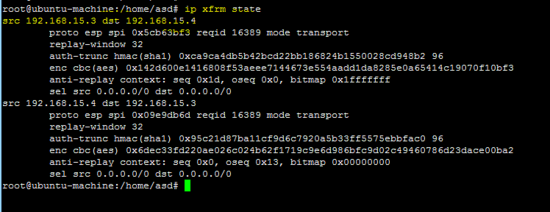
以下命令显示IPsec隧道状态
ip xfrm state
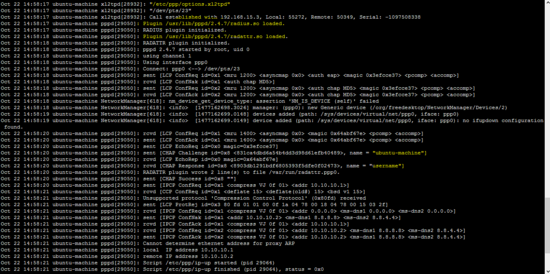
OpenSwan日志( /var/log/auth.log )和xl2tp日志( / var / log / syslog )也显示了L2TP VPN的状态。
tail -f /var/log/auth.log
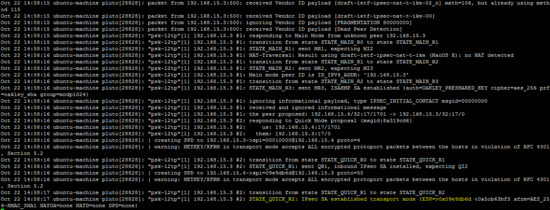
tail -f / var / log / syslog
在本教程中,第2层隧道协议与IPSec和Freeradius一起使用,以提供安全和身份认证机制。 使用基于Android的客户端来演示L2TP over IPsec的工作。








